Many companies get IT risk assessments simply because it is a regulatory requirement, however, they can also be a useful planning and budgeting tool. As a CFO in today’s technology landscape, there are so many methods of cyber-attacks and so many tools to prevent them, it is difficult to know what your company needs. You can never be 100% protected, but by learning where you are most vulnerable, you can start to put protections in place to mitigate your risks.
During an assessment, the company doing the assessment will review all your systems, policies, and procedures and processes to determine where your risk is and whether you have anything in place to protect your company. At the end of your assessment, you will receive a set of recommendations. These will include some simple items like implementing new policies or changing settings on some of your existing tools or equipment. There will also be more complex and expensive recommendations like installing new firewalls, re-configuring your network or rolling out company wide training. Most likely, you will not be able to do everything, and certainly not all at once. So, how do you prioritize which recommendations to do and when?
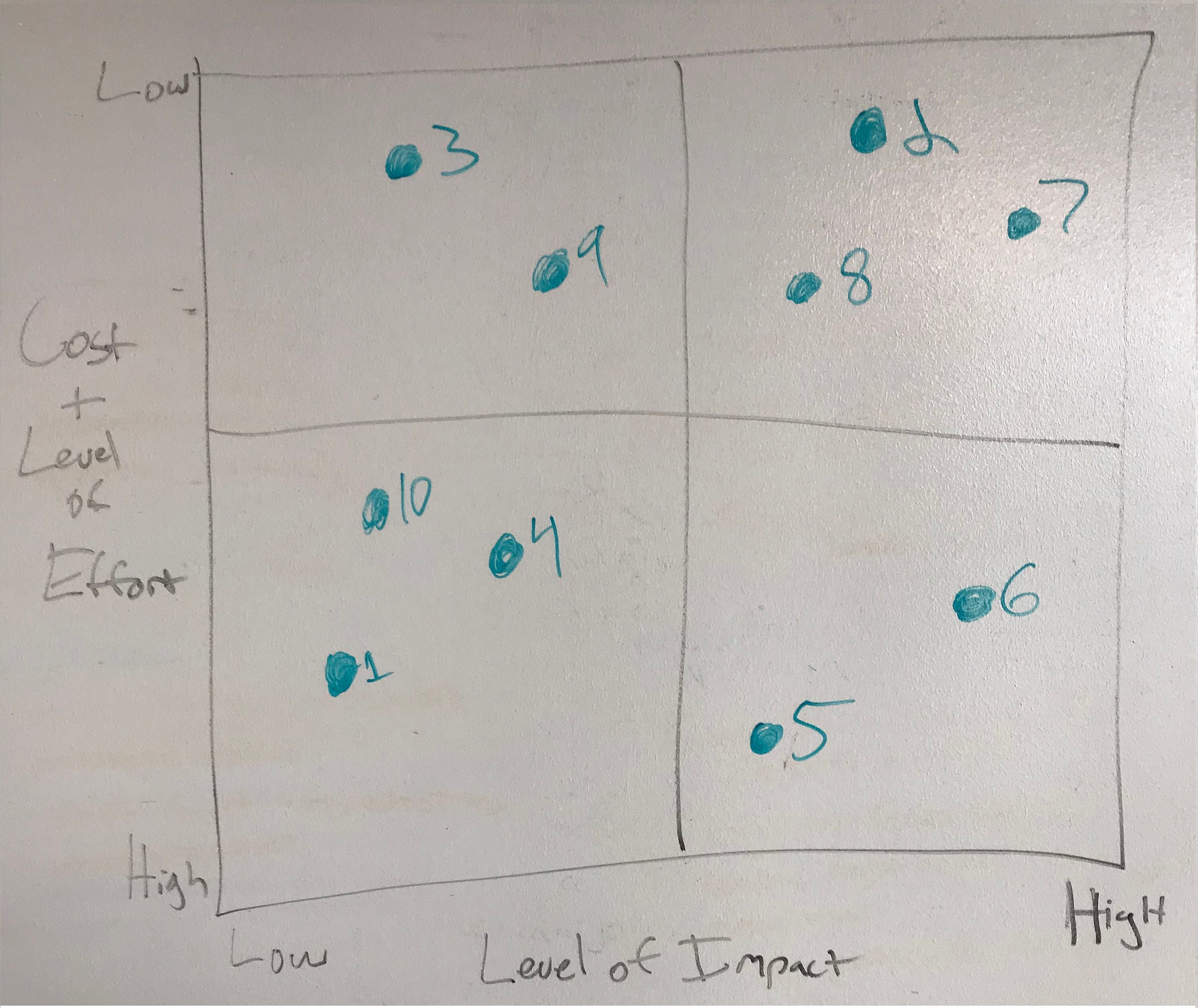
At Think|Stack, we like to use a matrix like the one pictured above. Each recommendation is assigned a level of impact, that is, how much it will increase protection or improve performance, on a 1–10 scale. Then a cost and level of effort is assigned to each. Once you assign those to each recommendation, you can plot them on the chart with low impact/high cost items on the bottom left, low impact/low cost items on the top left, high impact/high cost items on the bottom right and high impact/low cost items on the top right.
Items on the bottom left are low priority or items that you might never do. They cost a lot or require a lot of effort and the impact is minimal. Items on the top left have limited return but are low cost, so you will want to spend some time reviewing these. Items on the bottom right are high cost but also have a high impact. These are the items you will probably want to do as budget allows. Items on the top right are low hanging fruit. They don’t cost a lot or take a lot of effort but they will have a large impact. These should be the top priority items.
Cyber security and technology in general are constantly changing and it can be hard to keep up. A risk assessment can help you find your gaps and create a plan to fill them as your budget allows.
About the Author

Travis Sachse
CFO




